You can keep blocking yesterday’s hash, or you can start defending against tomorrow’s behaviour.
Most teams still live in the IOC loop: pull feeds, de‑dupe, push into SIEM/EDR, block and move on.
It works, until it doesn’t. Indicators burn fast; adversaries rotate infrastructure and re‑pack malware, and you’re back to square one. What endures is adversary behaviour: how attackers use techniques to get in, move, persist, escalate, and impact.
That’s what Threat‑Led Defense focuses on.Systematically mapping real adversary tactics, techniques, and procedures (TTPs) to your controls so you can see coverage, prove it, and improve it.
IOCs are concrete artefacts: a SHA‑256, a domain, a cert fingerprint, a registry key. They’re cheap to operationalise and great for triage and rapid blocking. They’re also brittle and short‑lived.
TTPs and adversary behaviours; LSASS credential dumping, PowerShell -enc living‑off‑the‑land, and scheduled task persistence. They’re harder for attackers to change and therefore better foundations for durable detections, hunts, and resilience. They demand richer telemetry and real detection engineering work that pays back.
Threat‑Led Defense doesn’t throw IOCs away; it prioritises TTP coverage and uses indicators as accelerants, not a strategy. MITRE ATT&CK provides the shared language to do this across teams, tools, and playbooks; it’s a knowledge base and mapping framework, not a compliance standard.
Coverage, defined without hand‑waving, is the explicit mapping between the adversary behaviours you care about and the people, process, and technology that would detect or stop them in your environment. A practical way to make this concrete is a Coverage Map that crosses your Threat Profile (which TTPs matter for your sector, footprint, and exposure) with your Defensive Stack (what controls you actually have, including gaps you suspect but can’t yet quantify).
The result exposes duplication, blind spots, and “paper coverage” detections that never fired outside a purple‑team day. From that clarity, you get prioritised detection engineering; build or upgrade detections where risk is highest and coverage is thinnest, stack optimisation that shows which tools map to which adversary behaviours so you can cut overlap or redundancy without introducing blind spots providing board‑level clarity that talks in adversary behaviours and risk reduction instead of feature lists.
The layer most teams lack is procedures. Even technique‑aligned detections can be vague; the real world runs on procedures, that is, how specific groups actually execute a technique in the wild. Procedure‑level mapping is where false positives fall and time‑to‑detection improves, because your content is tuned to how attackers operate, not what they do. If your coverage work stops at the technique name, you leave too much guesswork in tuning, too much noise in review cycles, and too many routes to failure when an actor changes a small implementation detail. Tightening the loop between threat intel reports, procedure extraction, and detection content is the difference between being threat informed and being ready.
A pragmatic blend that your team can run next looks like this
First, baseline with IOCs: use curated, scored feeds; enforce TTLs; enrich with source and confidence; and keep the set lean to avoid alert smog.
Second, level up with TTP detections: pick the top ten behaviours in your threat profile spanning initial access to impact; write detections mapped to ATT&CK; back them with the telemetry you actually have; and validate with emulation.
Third, hunt and iterate: pivot from single indicators to groups and campaigns of behaviours and infrastructure patterns; promote hunts that repeatedly catch the same behaviours into engineered detections; and track MTTR and false‑positive rate per TTP so you know which to harden next.
Finally, measure coverage, not noise: maintain a living Coverage Map and answer “can we defend against the threats that matter most in our environment?” with facts when a new campaign drops. That’s the signal leadership needs to fund the next fix.
Regulated organisations
Organisations in regulated industries are moving first because the reporting burden now expects threat‑led defence and evidence that your controls align with real adversary behaviour. Behaviour‑first coverage translates cleanly into governance views, audit evidence, and board communication without dumbing it down for practitioners.
It’s good security and good accountability. For financial services and other regulated sectors, it also makes DORA conversations concrete: which behaviours matter most, where your coverage is partial, and what the risk‑weighted next steps are.
You keep your stack; you gain objective visibility into how it actually defends. That independence matters when your job is defending outcomes, not a product catalogue. The platform accelerates the shift from IOC‑chasing to threat ‑led defence by making it easy to see what matters, aligning teams around a common language, and closing the highest‑value gaps first.
If you’re still IOC‑chasing, start here: bring your top threats, a list of your controls, and one or two thorny use cases andidentity abuse and data exfiltration that are common. Walk a Coverage Map, highlight the quickest threat‑led wins, and decide where to retire noise without losing defence.
Ready to take the next step?
If you’d like to run a pressure test with your data, we can put you in touch with a specialist who will organise a sample Coverage Map walkthrough aligned to TTPs and adversary behaviour based on your environment.
The moment you can answer “can we defend X against Y ?” with specifics, you’ll feel the shift in control from chasing to leading.
Introducing Threat-Led Defense
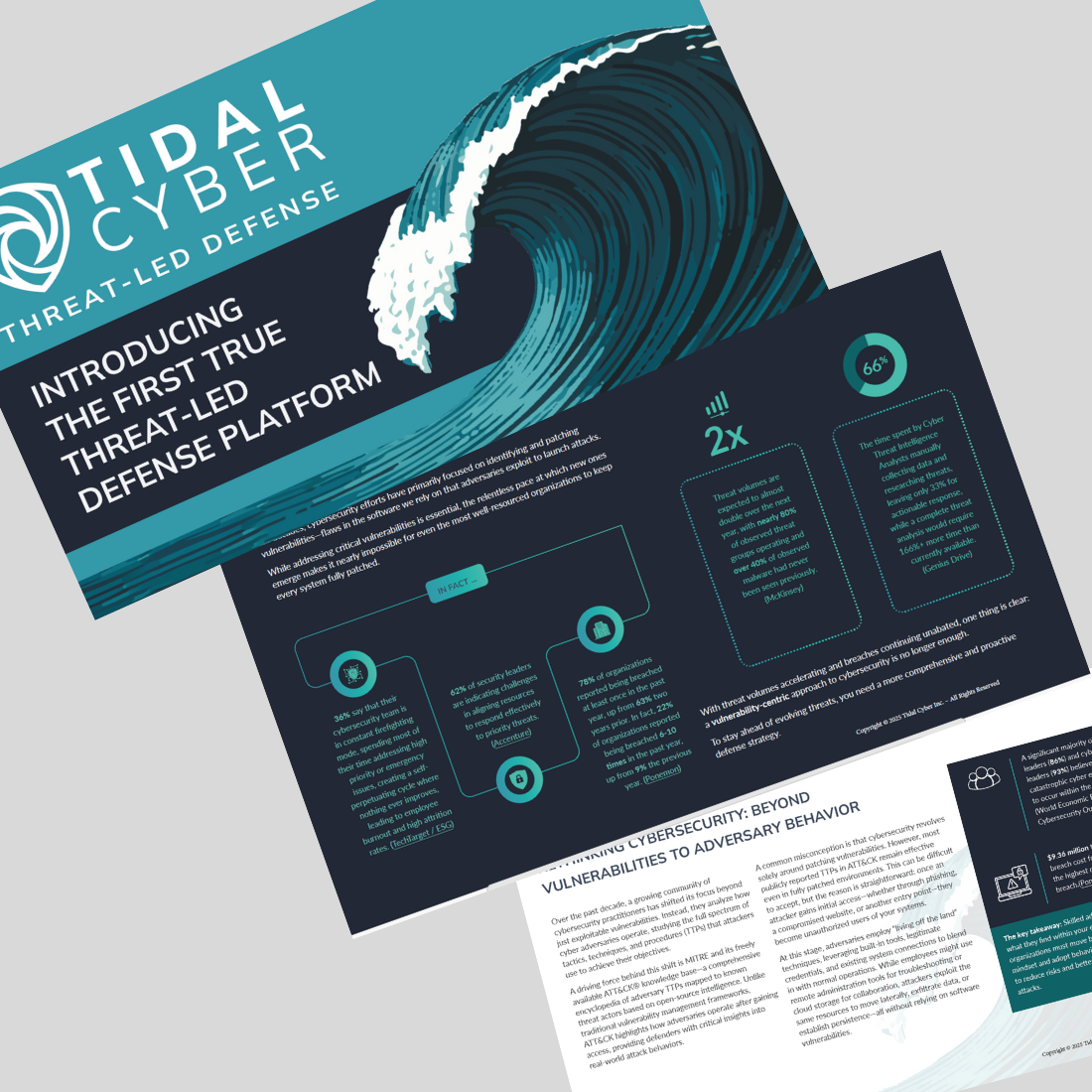
For decades, cybersecurity efforts have primarily focused on identifying and patching vulnerabilities—flaws in the software we rely on that adversaries exploit to launch attacks.
While addressing critical vulnerabilities is essential, the relentless pace at which new ones emerge makes it nearly impossible for even the most well-resourced organizations to keep every system fully patched.
Webcast: A new era in Threat-Led Defense begins here
Join Tidal Cyber’s co-founders for an exclusive fireside chat as they unveil the next evolution in cyber defense: Threat-Led Defense.
About this Sponsor
Built by the Team Behind ATT&CK® Tidal Cyber is powered by the practitioners who helped make MITRE ATT&CK® the industry’s common language for adversary behaviour.
With deep roots in ATT&CK stewardship, evaluation programs, and hands-on threat-informed defense, their team has productised the approach they pioneered, making it practical, scalable, and ready for your day-to-day defense.
More in Tidal Cyber
Book your discovery call now.
Techniques, procedures, adversary change.
from Tidal Cyber Community Edition to an Enterprise rollout.
When 'Good' looks THIS GOOD!
(and why you probably don't have it yet).
Between techniques & reality
Share this story