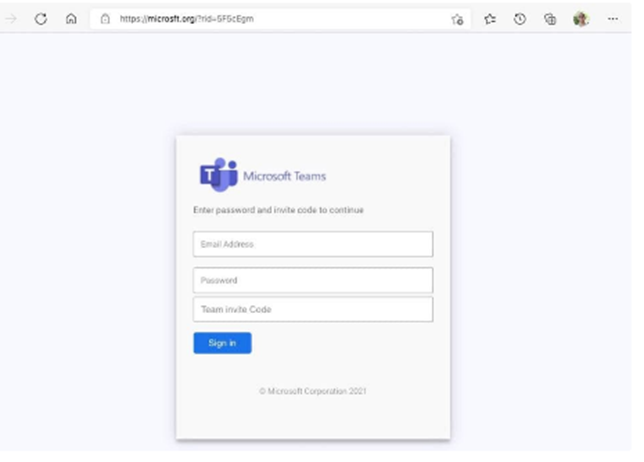
If you’re not paying attention, it’s just another Microsoft Teams login for that meeting you’re running late to. You just received the reminder and hurriedly enter your credentials. Surprise! You’ve just become a victim of phishing.
Do you know anyone like this? Would they immediately fill in the form with their credentials and invite code that just arrived in their inbox? While running late to an online meeting, would they notice the bad URL and realise that someone is trying to steal their credentials? There’s a pretty good chance they would not notice and fill in the requested information
Using phishing attacks, hackers prey on humans because we are the weakest link. We think the network and end-points are secure enough, so we don’t need to worry. That couldn’t be further from the truth.
According to Terranova Security, over 25% of phishing email recipients (ahem… humans) click on links inside phishing emails, and over 60% of those clickers (again… humans) submit data on pages similar to the image above. This is exactly why phishing has become the #1 attack threat vector. Humans are very likely to fall for these tactics!
The FBI received over 240,000 complaints for various phishing-type of attacks in 2020, which is over 200% more than 2019. Between phishing and other related email attacks, the FBI estimates losses exceeded $1.9B in 2020. 2021 is expected to be even worse.
One way to help combat these increasing attacks is to implement regular phishing awareness testing to identify employees who are clicking phishing emails and submitting sensitive data.
Libraesva PhishBrain provides an intuitive interface for administrators to coordinate recurring phishing campaigns aimed at targeted groups inside the organization. Simply populate a list of targeted mailboxes, including directly from Microsoft 365 or Google Workspace, choose from one of many modern and realistic phishing templates and landing pages, and set the timeframe for sending, reporting, and future recurrence. That’s it!
After each campaign, clearly see who poses the greatest risk for leaking data so appropriate action may be taken, such as record-keeping, training, and ongoing testing. PhishBrain will continuously update the risk score to provide up-to-date risk profiles for each targeted mailbox. Quick. Simple. Informative.
If you'd like any more information on this topic, feel free to request a callback from a specialist.
A CTO’s view
Email communications the use of geoblocking
Share this story
If this is a topic you want to know more about you can contact a specialist at NetUtils who will be happy to help you learn more
Let us know what you think about the article.
We're a community where IT security buyers can engage on their own terms.
We help you to better understand the security challenges associated with digital business and how to address them, so your company remains safe and secure.