Get free access to MYREDFORT'S VSOC for 3 months. No Commitment, No Contract, No Fuss
Get free access to MYREDFORT'S VSOC for 3 months. No Commitment, No Contract, No Fuss

There’s sometimes an underlying thought by small to medium sized businesses (SMB’s) that it’s really only a major concern for large corporations, banks and governments, because fraudsters committing the crimes go after the big bucks.
Yet the reality is, a virus wiping out an entire data set, or a disgruntled employee running off with critical business assets is much more likely and as just as devastating, for a small business. This has never been more relevant in the current boom-time of home-working.

This could include the cost for an entire business IT infrastructure being off-line while bought in consultants and the IT team try to get it back up and running, as well as post breach action required to assess what has been accessed that often lead to non-compliance fines.
Download the Solution BriefFraudsters recognise that the majority of businesses have basic measures in place, and prey on the fact that very few businesses do anything above and beyond these basic measures. So much so that over 90 per cent of cyber-related incidents are caused by user error.
With ever-evolving threats, it is important that owners of companies of all sizes not only seek to protect their business, but also begin to change their mindsets from ‘it won’t happen to us’ to ‘it’s not if, but when’.
Problems occur when firewalls are neglected or badly configured, there’s an over-reliance on anti-virus, or there’s a lack of attention to what staff are plugging into the network, to name but a few.
Even if the sudden surge in remote working hadn’t happened, SMB’s are at risk because they can’t see happening in their network.
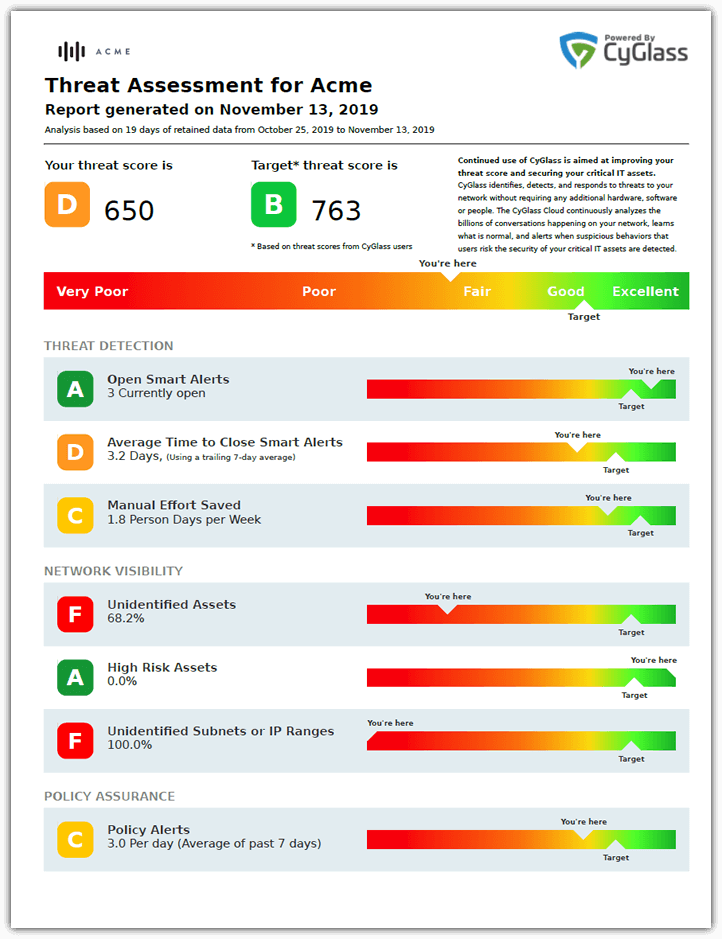
The VSOC is an affordable solution that provides:
The VSOC wraps all of this capability easy to understand Executive Summary Report, so you and you team can measure their progress.
And getting your business through it: Cyber Security Edition
When Office 365 isn't secure enough
You can’t protect what you can’t see
Alarm bells should be ringing with cyber security teams following recent guidance issued by both UK and US government security experts.
Before Covid 19, many SMB’s and mid sized enterprises were embarking on a journey to workplace automation and a world of greater performance, flexibility and control
With more employees now working from home, the risk of breaches has grown exponentially.
Some think that hackers are "cool" and that their spirit of mischief and sneaking is admirable.
50% of IT leaders don’t know if their cyber security is working
Any business feels the pain