Share this story
Read Time: 2 minutes
Without being alarmist, the reality is the current situation’s creating a perfect storm for cybercriminals.
Globally, there’s never been a better time to take advantage of cyber security vulnerabilities while overstretched IT teams are looking the other way. Contrary to popular belief, Fraudsters don’t just go after the big guy’s, they go after what’s easy.
Here we aim to outline the different stages of a crisis and the minimum steps you need to consider from a cyber security perspective to ensure one crisis doesn’t lead to another.
Business Un Usual
Firstly, the positive conclusion is we’re going to get through it. The decisions successful businesses make now will have an impact on how great their recovery will be and how long it will take.
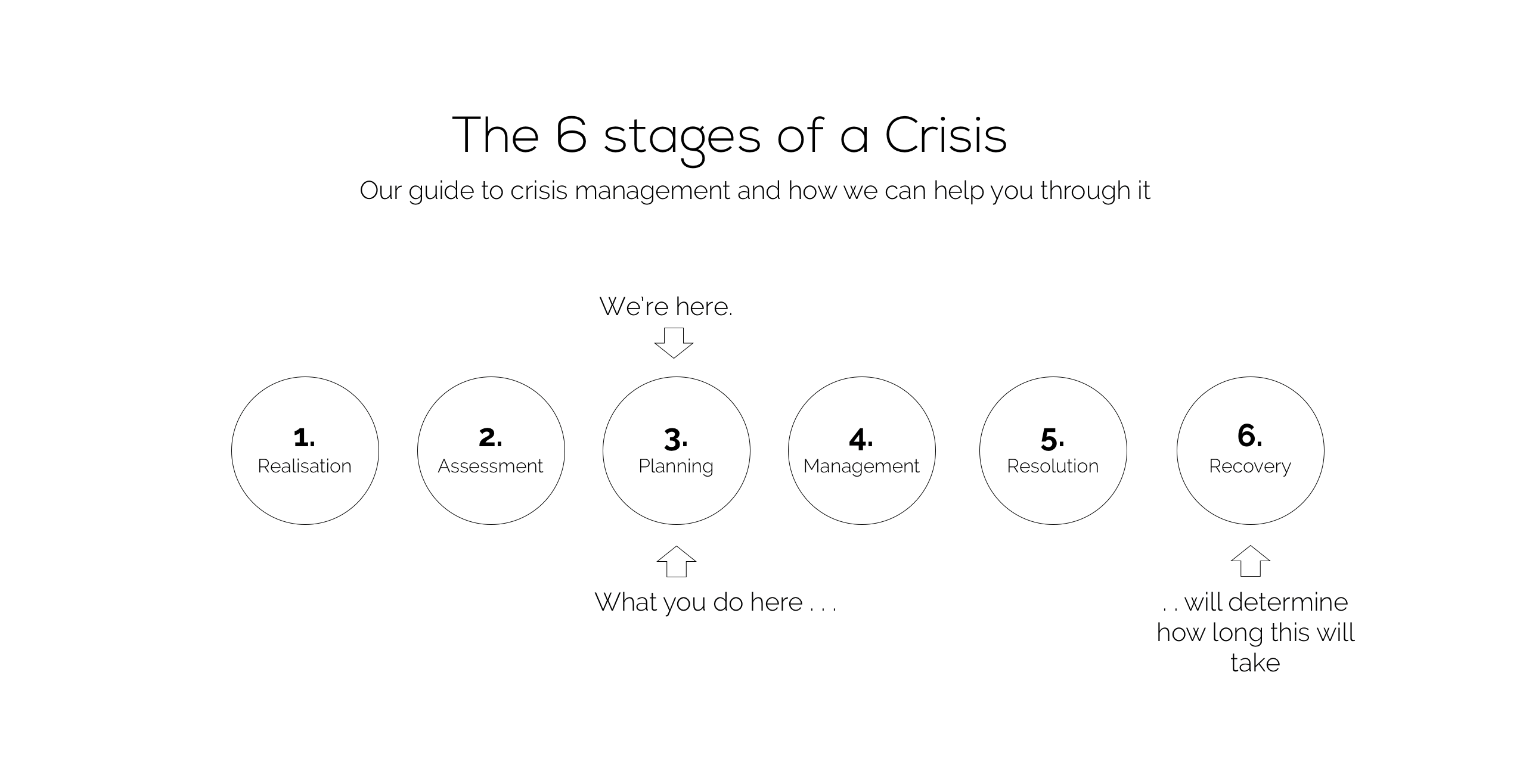
Today, we’d say we’re at the planning stage, with businesses working out what the landscape looks like and what they need to do to ensure business continuity.
As we all know, the primary factor resulting from the crisis is ’Social Distancing’ which requires everyone to still able to work should do so at home. Almost overnight, home working has become the nationwide norm. IT teams have done a sterling job covering a great deal of ground in a short period of time to keep their businesses functioning.
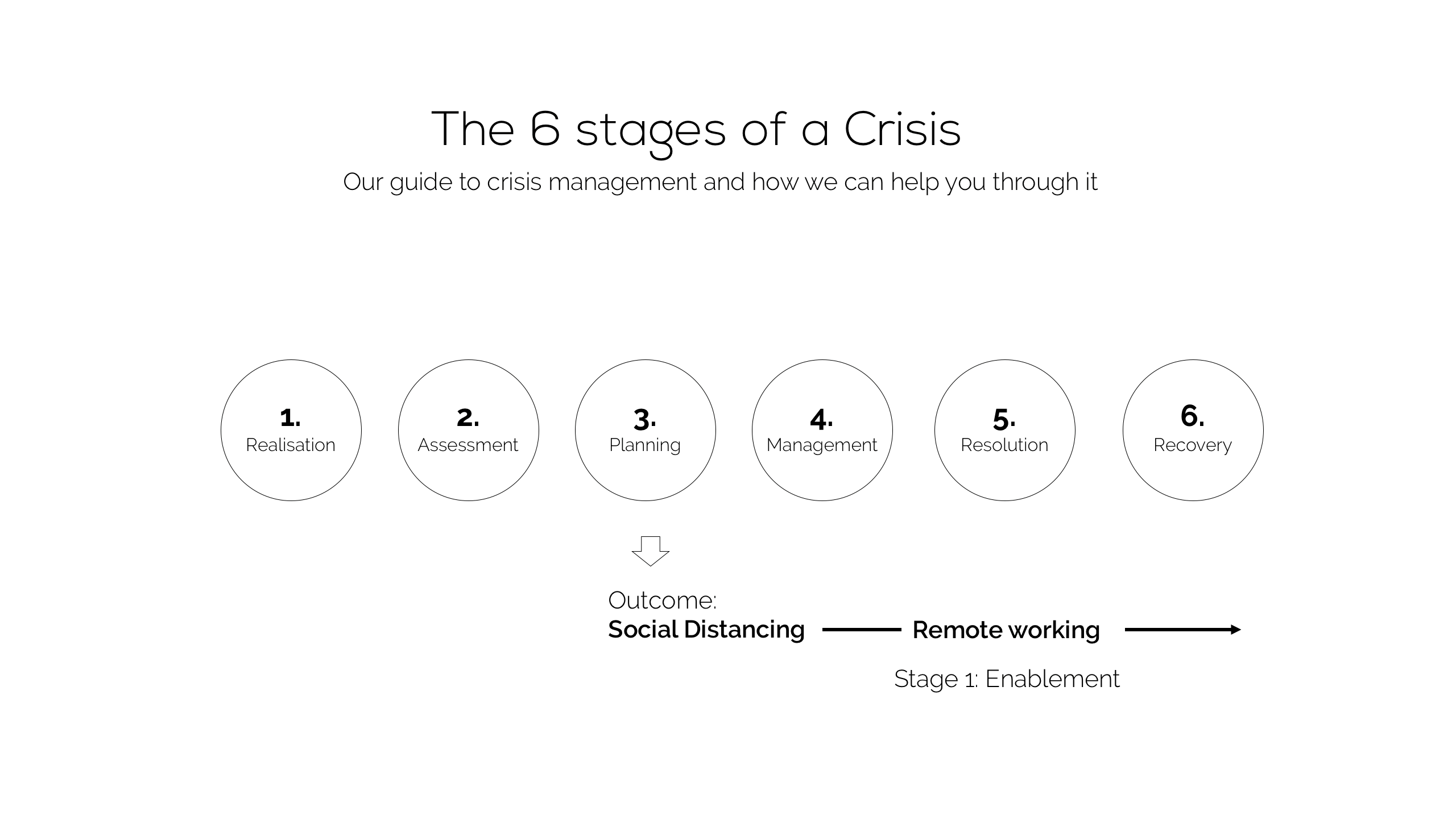
Stabilising the Security Landscape
Once this intense set up period is completed, businesses must consider how to maintain their businesses through the Management and Resolution stages. Key here is to ensure it’s protected from any additional threats that could disrupt what is already a delicate balance between continuity and failure. Standard cyber security practice is even more crucial to this balance than ever before.
You can’t Protect What you Can’t See
Right now, businesses need visibility of exactly what’s going on in their network. If they can’t see it, they can’t protect themselves from it.
Already cyber security teams are reporting an upsurge in rogue activity which occurs when legacy firewalls are neglected or badly configured, over-reliance on anti-virus, or there’s a lack of attention to what staff are plugging into the network.
Yet there’s a balance to strike. We understand setting up numerous home workers is an unplanned expenditure and funds from other much needed projects will most likely have been diverted.
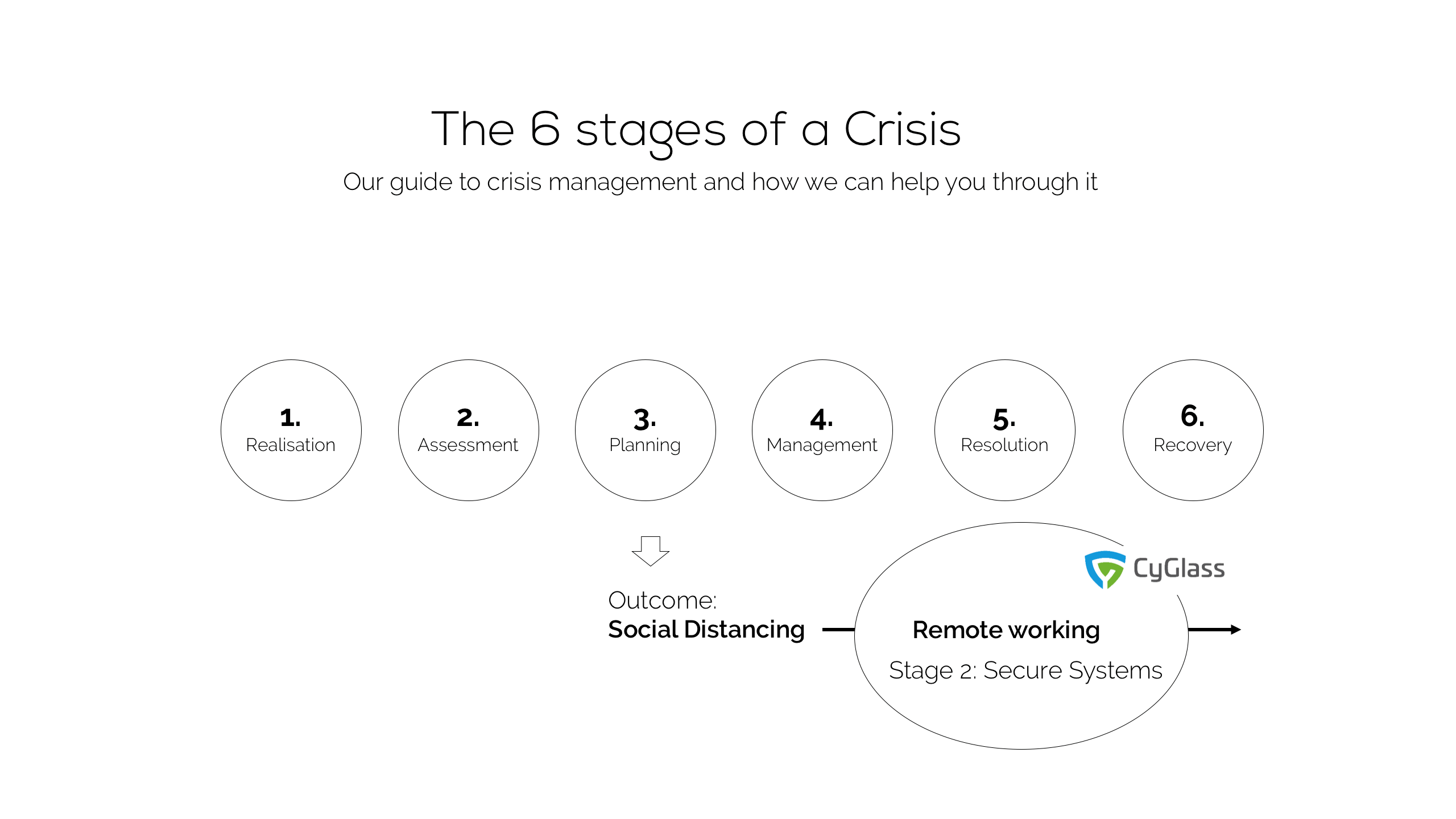
Be in Control and Keep Recovery on Track
Because of this, we are using our relationship with a leading cyber security vendor to offer a remote visibility assessment on a 3-month trial so they can see what’s going on across these new and diverse remote networks.
Our aim is to help keep business Recovery on track. It’s right for everyone. The last thing any business needs right now is damage to brand reputation caused by data loss or system downtime, or fines for non-compliance.
Let us know what you think about the article.











