Share this story
Read Time: 6 minutes
Are you curious about the value and benefits of XDR in your environment? Has your board of directors ever asked: How did this happen? Did we know about this criminal and anything they may have been up to? Were we the only targets? MVISION XDR has the answers!
Imagine, if you will, a scene straight out of one of your favourite impossible mission movies. The background music is driving a suspenseful beat while the antagonist attempts to steal the latest technology from a very favoured industry competitor called Rad-X Incorporated.
It’s a trade secret that will change the industry forever, and if the villain achieves her mission, she will hold the future of aviation in the palm of her hand. She’s bypassed laser motion detectors, swung from the ceiling to avoid floor placed pressure plates, and even performed some seriously intense acrobatics to slip through video surveillance mechanisms. Then, at the apex of suspense, while the music ascends to a crescendo, a hard thumping release, she reaches out to grasp a microchip placed in the centre of the room on a pedestal as if the room were designed only to show off its magnificence. As her fingers gently nestle against the circuit… the music stops, the alarms sound, and she walks out completely and utterly undisturbed!
All the components in this scene were meant to record and detect when activity occurs. But when we needed it most of all that it amounts to is a noisy detection capability. It did not actually “prevent” the malicious actor from doing anything. Instead, the system merely let everyone know that it occurred… very anticlimactic if you ask me, and frankly not very useful if you’re the good guy.
Deconstructing the SIEM, Log by Log
SIEM technologies have been used in security operations for over 15 years for a few reasons. First, SOCs must be able to tell a story while performing incident response investigations. And to go back in time effectively, logged events of these activities can be more easily accessed if the events are stored centrally and for appropriate longevity. So, when the police show up, the victim can accurately name the perpetrator. Next, because the data sources are so disparate, SIEMs can be used to correlate activities among usually unrelated feeds. For example, if a floor plate is triggered, then a motion sensor fires within 15 seconds of each other, their collective severity may raise more of an alarm. And thirdly, centrally reporting on collective data allows the business to identify where it is effectively investing in control technologies. In this extended example, the victim can run a report monthly showing that the microchip pressure sensor triggered 5 times this month, while the others may have triggered only once or twice. Certainly, all these capabilities are just as important today as they were in 2005.
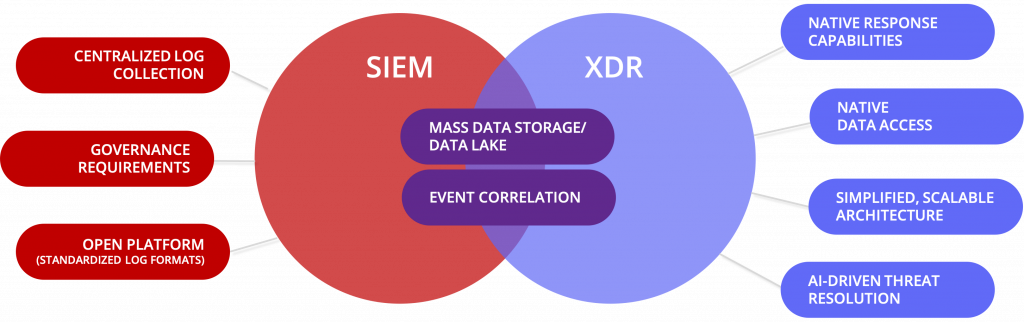
But there is one glaring gap: why isn’t there a better way to take corrective action after the incident occurs? Extended Detection and Response (XDR) capabilities have some similar outcomes as we would expect in 2021, but with an added response component… and in McAfee’s case, many response components. Some capabilities overlap SIEM’s, which is natural based on each use case, but both of which are still essential to the modern security operations program.
If You See Something, Do Something
While SIEM technologies, for the most part, allow its administrators to integrate through APIs with other technologies, the actions available are often limited in nature and fail to provide a seamless and consistent response option across the landscape. XDR, however, does just that. The platform is designed such that whether the system on which you are acting is an endpoint, network component, or cloud service, the security operations practitioner should expect to enjoy an intimate level of native control on that security control device. Performing actions like restricting further access, retrieving additional information, or gaining console capabilities should be as simple as a click of a button. With XDR, when the alarm sounded, Rad-X would have been able to simply click a button to lock the vaulted room and apprehend the perpetrator.
And since this is a differentiator between XDR and SIEM platforms, it should stand to reason that response capabilities should be a key factor when comparing XDR providers. McAfee offers some of the most robust response capabilities right out of the box such as quarantining affected assets, while simultaneously offering the ability to write your own for Windows, MacOS, or Linux.
Go Where The Data Is – At the Source
While it is painfully apparent that data entering data lakes and massive data collections are regularly changing, data types are changing almost as frequently. SIEM technology, which is heavily based on collectors, parsing, enrichment, ontology, and more, often fails to address the ongoing change of data types on the data source. This means that the collectors need to be updated frequently. However, what if the data was first triaged and analysed at the source and the results delivered to the collection and correlation points? This would address a large portion of the data type challenge while simultaneously expecting and embracing the idea that the data will continue to live at its source. Sure, there may be cases where the raw data needs to be shipped to mass storage for historical searching and hunting, but those are the minority of the cases. And, since the goal of XDR is not to meet log retention requirements as a compliance tool, it need not focus on collecting all events created.
When running a search in XDR platform, such as McAfee’s MVISION XDR, the searches can be run against mass storage or in real-time. Realtime searches allow the data source to perform the query against the raw origination of the event. And, since both capabilities are available, comparing deltas between the state of the data source is easily done. If Rad-X, were using XDR they would be able to ask questions of the corridors, cameras, and entryways the villain was using throughout the attack. Instead, they were forced to wait for an event significant enough to have occurred to be alerted that the incident was now in the past.
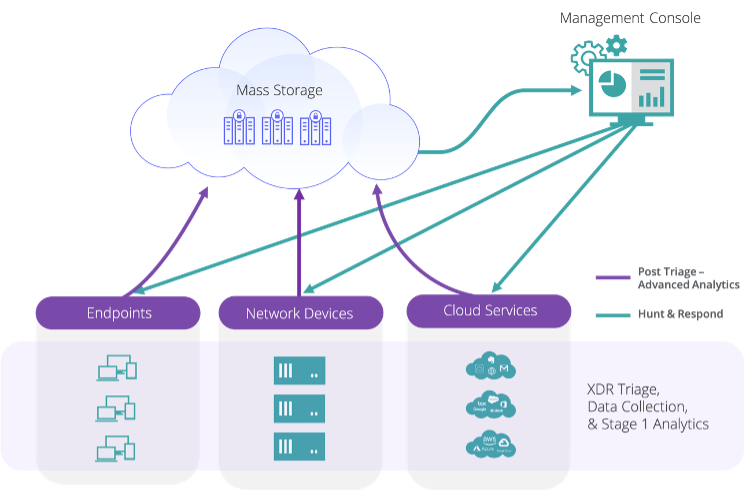
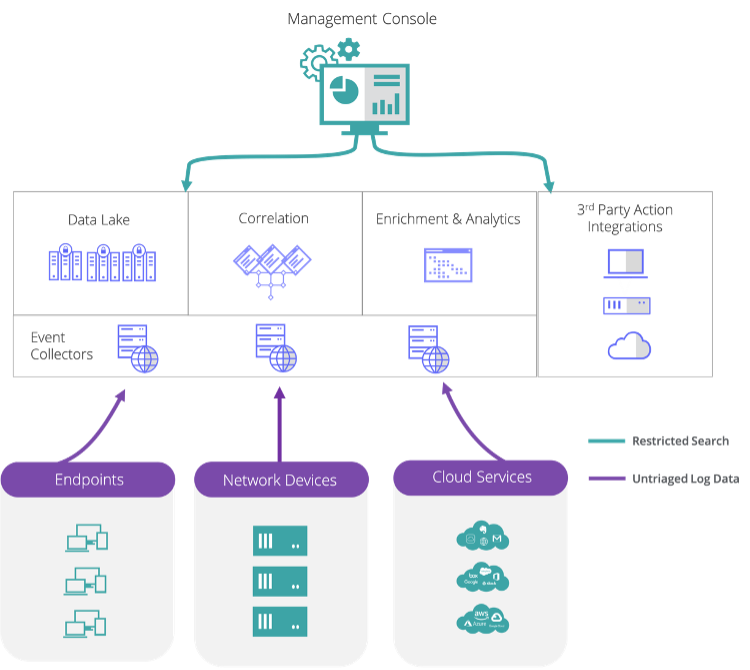
As you can tell from the illustrations above, XDR offers security teams a simpler cloud-native service architectural model when compared to traditional SIEM. The majority of SIEM deployments require all the native infrastructure to be deployed as on-premises software or appliances or in IaaS. XDR can reduce the complexity of your security configuration and the expert resources required to operate it.
Hot Pursuit: A Proactive Approach to Finding Threats
Rad-X’s CEO wants answers, and he wants them now! How did this happen? Did we know about this criminal and anything she may have been up to? Were we the only targets? What is our best course of action to investigate what happened here?
MVISION XDR is designed to answer exactly these questions.
MVISION XDR goes beyond consolidation of endpoint detection and response (EDR), network detection and response (NDR), and cloud detection and response capabilities as it leverages threat intelligence and analytical posture assessments from MVISION Insights to guide its ability to predict, to prescribe, and to help prioritize what’s most important in your organization. MVISION Insights would help Rad-X shift its focus left of the moment of impact by telling its defenders about the pending threats from the threat actor. Knowing that she was targeting aviation innovators and that Rad-X was in her line of sight would have helped, but it would also call out the gaps in defence capabilities based on her techniques and procedures.
Then, even if the incident were to still have occurred, MVISION XDR would be able to take advantage of its Artificial Intelligence data analytics by examining how the intruder behaved, what kind of artefacts were left behind on the floor, and what may be missing from the environment which “should” be there. It’s like having a virtual Sherlock Holmes analysing each of your XDR incidents across endpoints, network, and cloud environments.
Mission Accomplished: Go Beyond the Limits with MVISION XDR
Rad-X suffered an unfortunate event, but they learned an incredibly valuable lesson: SIEM is important as it meets some critical functions, but XDR is more appropriate in performing action-driven investigations, threat analytics, rapid response, and more. So, if you find yourself in a position like Rad-X and are curious about the value and benefits of XDR in your environment, take a page out of Rad-X’s playbook and consider MVISION XDR to provide a shift left in threat predictions, prescriptions, and prioritization. Consider MVISION XDR to enhance your incident analytics capabilities with cloud-based AI playbooks. And consider MVISION XDR to provide detection and response capabilities from device to cloud.
Let us know what you think about the article.


